Never Trust, Always Verify: Your Complete Introduction to Zero Trust Security
Modern Cybersecurity Redefined: How Continuous Verification and Least Privilege Access Protect Your Business in a Cloud-First, Remote-Work World
In an age where cyber threats evolve faster than traditional defenses can adapt, organizations worldwide are abandoning the outdated “castle-and-moat” security model in favor of a revolutionary approach: Zero Trust. Imagine a security framework so robust that it assumes every user, device, and network connection could be compromised—and continuously verifies everything, everywhere, all the time. This isn’t paranoia; it’s the future of cybersecurity, and it’s transforming how businesses protect their most valuable assets in our increasingly connected, cloud-first world.
Digital shield representing cybersecurity and network protection with integrated circuitry design.
The shift to Zero Trust represents more than just a technology upgrade—it’s a fundamental reimagining of cybersecurity philosophy. Born from the recognition that perimeter-based defenses have become laughably inadequate in the face of sophisticated attacks, remote workforces, and cloud migration, Zero Trust has evolved from a theoretical concept in 2010 to a business imperative embraced by 89% of organizations today. With the average data breach now costing $4.45 million globally, and companies with mature Zero Trust implementations reporting 50% lower breach likelihood, the business case for this security paradigm has never been clearer. This article will guide you through everything you need to understand about Zero Trust—from its foundational principles to real-world implementation strategies—empowering you to make informed decisions about securing your organization’s digital future.
Understanding Zero Trust: Breaking Free from Perimeter Thinking
The Evolution from Castle Walls to Continuous Verification
For decades, cybersecurity operated on a simple premise: build strong walls around your network, and everything inside those walls could be trusted. This perimeter-based security model treated networks like medieval castles—hardened on the outside with firewalls and intrusion detection systems, but soft and vulnerable on the inside. Once an attacker breached the perimeter or an insider turned malicious, they could move freely through the network, accessing sensitive data with minimal resistance.
The concept of Zero Trust emerged in 2010 when John Kindervag of Forrester Research recognized this fundamental flaw. He observed that traditional security suffered from what he colorfully termed the “M&M problem”—hard and crunchy on the outside, but soft and chewy on the inside. Kindervag’s radical proposition was to eliminate the “soft chewy center” entirely, making security ubiquitous throughout the network rather than concentrated at the perimeter.
The timing was prescient. The same year, Google launched BeyondCorp following a sophisticated cyberattack on their infrastructure, demonstrating that even technology giants weren’t immune to perimeter breaches. This convergence of thought leadership and practical necessity accelerated Zero Trust from theoretical framework to operational reality. By 2020, the U.S. government formalized its commitment through Executive Order 14028, mandating federal agencies adopt Zero Trust Architecture while strongly recommending private organizations follow suit.
Core Philosophy: “Never Trust, Always Verify”
At its heart, Zero Trust operates on a deceptively simple principle: “never trust, always verify”. Unlike traditional models that grant implicit trust to anything inside the network perimeter, Zero Trust assumes that threats exist both inside and outside organizational boundaries. Every user, device, application, and data flow is flagged as untrusted by default and requires constant verification before accessing resources.
This represents a profound philosophical shift. Traditional security asked, “Are you inside or outside our network?” Zero Trust asks, “Can you prove right now, at this specific moment, that you should access this specific resource?”. The distinction transforms security from a binary state (trusted/untrusted) to a continuous evaluation process that adapts to changing contexts and threats.
The philosophy manifests through several interconnected principles that collectively create a resilient security posture:
Explicit verification requires organizations to authenticate and authorize based on all available data points—user identity, device health, location, time of access, and resource sensitivity. A login attempt from an employee’s usual office location during business hours carries different risk than the same credentials accessed from a foreign country at 3 AM.
Least privilege access ensures users and systems receive only the minimum permissions necessary to perform their functions, dramatically limiting potential damage from compromised accounts. If a marketing employee’s credentials are stolen, the attacker shouldn’t gain access to financial databases or engineering systems.
Assume breach operates under the understanding that attackers may already be inside the network, driving investment in detection, containment, and rapid response rather than prevention alone. This mindset fundamentally changes defensive strategy from “if we’re breached” to “when we’re breached,” ensuring organizations prepare accordingly.
The Catalyst: Why Traditional Security Failed
Several converging pressures rendered perimeter-based security increasingly obsolete. The proliferation of cloud computing dissolved the notion of a defined network boundary—critical applications and data now reside across multiple cloud providers, making perimeter defense meaningless. Remote work accelerated dramatically, especially during the COVID-19 pandemic, placing trusted employees outside the protected perimeter while still requiring access to sensitive resources.
The explosion of Internet of Things (IoT) devices, mobile endpoints, and bring-your-own-device (BYOD) policies created thousands of potential entry points that traditional perimeters couldn’t effectively monitor. Meanwhile, attackers evolved sophisticated techniques to bypass perimeter defenses entirely—phishing campaigns targeting employee credentials, supply chain compromises, and zero-day exploits rendered the “hard shell” increasingly porous.
Perhaps most critically, the perimeter model’s implicit trust enabled devastating insider threats and lateral movement attacks. Once attackers compromised a single endpoint or recruited a malicious insider, they could traverse the entire internal network undetected, exfiltrating data or deploying ransomware across the organization. The average breach detection time of 194 days highlighted how traditional monitoring failed to catch threats that had already penetrated the perimeter.
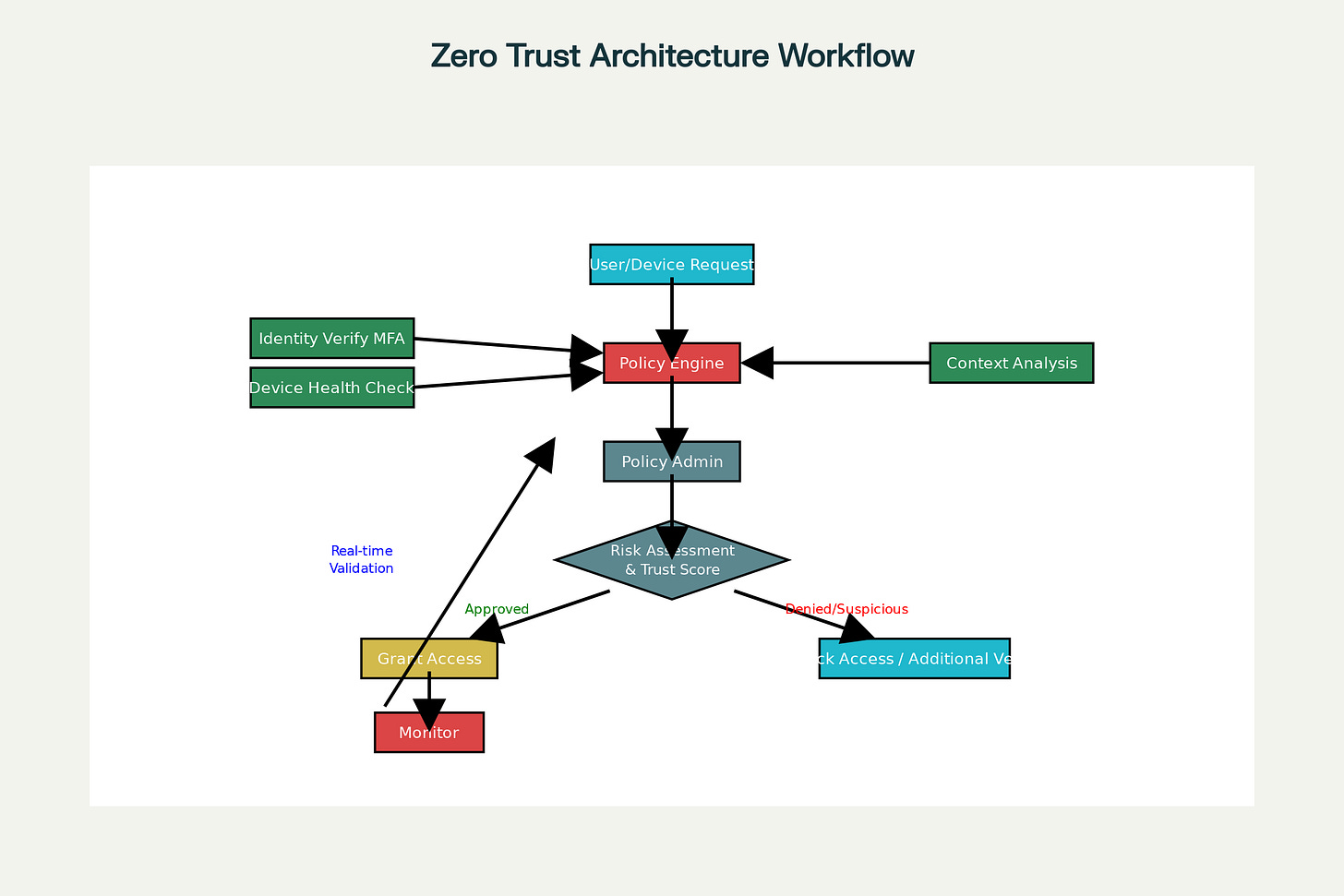
Zero Trust Architecture Workflow - Continuous Verification Process
The Architecture of Zero Trust: Components and Technologies
Seven Pillars of Zero Trust Protection
Zero Trust isn’t a single product you can purchase and install—it’s a comprehensive architectural framework composed of multiple integrated components working in concert. Understanding these foundational elements helps organizations assess their current capabilities and identify gaps in their security posture.
Identity and Access Management (IAM) forms the cornerstone of Zero Trust, managing digital identities and controlling who can access what resources. Modern IAM systems integrate with directories like Active Directory or cloud identity providers, centralizing credential management across on-premises and cloud environments. They enforce role-based access control (RBAC) and increasingly incorporate context-aware policies that evaluate factors like user behavior, device health, and location before granting access.
Multi-Factor Authentication (MFA) adds essential security layers by requiring users to present multiple forms of verification—something they know (password), something they have (hardware token or smartphone), and something they are (biometrics). Advanced MFA solutions support adaptive authentication, evaluating contextual signals to determine whether additional verification is necessary. A user accessing files from their usual device and location might only need a password, while the same user connecting from an unfamiliar country would trigger additional authentication challenges.
Microsegmentation divides networks into smaller, isolated zones with strict access controls between segments. Unlike traditional network segmentation that creates large zones, microsegmentation can isolate individual workloads or applications, preventing lateral movement even if one segment is compromised. Software-defined networking (SDN) enables dynamic micro-segmentation that adapts policies based on real-time risk assessments.
Device Security and Endpoint Management ensures that only healthy, compliant devices can access network resources. This includes continuous monitoring of device posture—whether operating systems are patched, encryption is enabled, security software is running, and no malware is present. Device authentication often uses cryptographic certificates issued during onboarding, providing hardware-level identity verification.
Data Security protects information at every stage—at rest, in transit, and in use—through encryption, classification, and access controls. Zero Trust data security ensures that even if attackers access storage systems, encrypted data remains unusable without proper authorization. Data classification helps organizations apply appropriate protection levels, with the most sensitive information receiving the strictest controls.
Real-Time Monitoring and Analytics provides continuous visibility into user behavior, network traffic, and resource access. Advanced solutions use artificial intelligence and machine learning to establish behavioral baselines, detecting anomalies that could indicate compromise—unusual data downloads, access attempts to unauthorized resources, or login patterns inconsistent with historical behavior.
Policy Engines and Enforcement Points make real-time access decisions based on predefined rules and risk assessments. The policy engine evaluates each access request against organizational policies, threat intelligence, and contextual factors, calculating a trust score. Policy enforcement points—whether network gateways, application proxies, or cloud access security brokers—implement these decisions, granting or denying access accordingly.
The NIST Zero Trust Framework
The National Institute of Standards and Technology (NIST) formalized Zero Trust principles in Special Publication 800-207, providing authoritative guidance that has shaped implementations worldwide. The NIST framework defines three logical components that form the decision-making core of Zero Trust architectures:
The Policy Engine (PE) serves as the central decision-maker, determining whether to grant access based on organizational policies and supporting data sources. It calculates trust scores by integrating inputs from identity systems, threat intelligence feeds, continuous diagnostics systems, and real-time risk assessments. For instance, if a user’s credentials appear in a recent data breach, the PE factors this into its access decision.
The Policy Administrator (PA) acts as the bridge between decisions and enforcement, implementing the PE’s determinations by configuring access permissions and managing session lifecycles. For approved requests, the PA issues secure tokens granting temporary access. If context changes during an active session—such as detecting suspicious behavior—the PA can immediately terminate access or prompt reauthentication.
Policy Enforcement Points (PEP) sit at the gateway to resources, blocking or allowing access based on PA instructions. These enforcement mechanisms can be physical devices like next-generation firewalls, virtual appliances, or cloud-based proxies, ensuring policies are consistently applied regardless of where resources reside.
NIST also published SP 1800-35 in 2025, providing practical implementation guidance developed through collaboration with 24 technology vendors. This comprehensive resource demonstrates 19 different Zero Trust implementations using commercial and open-source products, showcasing how organizations can apply Zero Trust principles across diverse environments—from on-premises data centers to multi-cloud architectures.
Three Primary Deployment Approaches
Organizations can implement Zero Trust through multiple architectural patterns, each offering distinct advantages depending on specific requirements and existing infrastructure:
Enhanced Identity Governance emphasizes identity and attribute-based access control, ensuring access decisions are tightly linked to user identity, roles, and contextual factors. This approach leverages strong IAM platforms, integrating with single sign-on (SSO) and conditional access policies to enforce least-privilege principles. It’s particularly effective for organizations with mature identity management capabilities looking to extend those investments into Zero Trust.
Micro-segmentation uses intelligent network devices—firewalls, smart switches, or specialized gateways—to isolate and protect specific resources. This network-centric approach prevents lateral movement by creating granular security zones, with each zone protected by policy enforcement points that scrutinize traffic attempting to cross boundaries. Organizations with complex on-premises infrastructure often find micro-segmentation an effective path to Zero Trust.
Software-Defined Perimeter (SDP) creates a software overlay that protects infrastructure by making it invisible to unauthorized users. Also known as Zero Trust Network Access (ZTNA), this approach connects users directly to specific applications rather than the network itself, eliminating the broad network access that VPNs traditionally provided. SDP excels in cloud and hybrid environments where protecting distributed workloads is paramount.
Secure Access Service Edge (SASE) has emerged as a fourth deployment model, integrating network and security functions into a unified, cloud-delivered service. SASE combines ZTNA, secure web gateways, cloud access security brokers, and firewall-as-a-service, providing comprehensive Zero Trust capabilities particularly suited for organizations with significant cloud adoption and distributed workforces.
Real-World Applications: Zero Trust in Action
Securing Remote Workforces
The explosion of remote work transformed Zero Trust from a forward-thinking concept to an operational necessity. Traditional VPN-based remote access exposed organizations to significant risks—employees connecting through VPNs gained broad network access, creating opportunities for compromised credentials to enable devastating breaches.
Zero Trust fundamentally reimagines remote access by applying strict authentication and access controls regardless of user location. Rather than granting network access, Zero Trust solutions connect remote employees directly to specific applications and data they need, nothing more. This application-level access eliminates the broad network visibility that VPNs provided, dramatically reducing attack surface.
Consider a practical example: A global company with 100+ remote employees across 14 countries implemented Zero Trust using context-aware authentication. Employees’ identities are verified based on geographical location, time of access, and IP address—not just credentials. The system provides continuous verification throughout sessions, preventing session hijacking. Device compliance checks ensure remote devices meet security standards, running updated software and proper configurations. Role-based access control strictly limits what each employee can access based on their job function.
The productivity benefits surprised many organizations. Users often experience faster application access after eliminating VPN bottlenecks—one deployment saw 3× faster access speeds. Employees can work securely from any location without the frustration of slow VPN connections or complicated access procedures.
Protecting Cloud Applications and Multi-Cloud Environments
Cloud migration poses unique security challenges that traditional perimeter defenses can’t address. Applications and data reside across multiple cloud providers, accessed by users from various locations and devices—there’s simply no perimeter to defend. Zero Trust provides consistent security policies that follow applications and data regardless of where they reside.
Organizations implementing Zero Trust in cloud environments leverage identity providers and context-aware controls to secure every application interaction. Access policies evaluate user identity, device health, and contextual factors before granting permissions to cloud resources. This approach prevents unauthorized access and data leakage even as workloads move between clouds.
However, multi-cloud Zero Trust implementations face significant challenges. Managing policies across different cloud platforms emerged as the top challenge for 49% of organizations, as each provider has unique tools, interfaces, and security requirements. Cost and resource requirements concern 48% of respondents, emphasizing the investment needed to implement Zero Trust at scale. Achieving visibility across all environments challenges 34% of organizations, hindering effective threat detection and response.
Despite these challenges, the benefits are substantial. Organizations with mature Zero Trust report 83% improved visibility and control over cloud applications, remote users, and bring-your-own-device scenarios—without compromising user experience. The ability to secure cloud applications while maintaining agility has made Zero Trust essential for digital transformation initiatives.
Safeguarding Critical Infrastructure
Critical infrastructure—healthcare systems, energy grids, manufacturing facilities—faces growing cyber threats from sophisticated attackers and malicious insiders. These environments often include legacy operational technology (OT) systems that lack modern security features, creating significant vulnerabilities.
Zero Trust applies rigorous segmentation, explicit authentication, and access validation to protect these sensitive environments. Legacy systems that can’t support modern security features are protected by isolating them in microsegments and strictly controlling communications with other systems. Access to critical controls requires multi-factor authentication and continuous behavioral monitoring to detect unauthorized activities.
One healthcare implementation demonstrates Zero Trust’s value in protecting medical devices. Traditional network models allowed medical devices broad access once connected, creating risk if devices were compromised. The Zero Trust architecture places firewalls directly in front of medical devices, blocking unnecessary traffic while maintaining required communications. Though this approach increases latency slightly, the performance boost from reduced network-wide traffic balances the impact.
The assume-breach principle proves particularly valuable in critical infrastructure. By operating under the assumption that attackers may already be present, Zero Trust implements continuous monitoring and strict containment measures that limit potential damage. Security teams achieve fine-tuned visibility, swift threat detection, and the ability to enforce compliance requirements that are often stringent in regulated critical infrastructure sectors.
Preventing Credential-Based Attacks
Credential theft through phishing, password reuse, or data breaches remains one of the most common attack vectors. Traditional security often treats valid credentials as sufficient proof of legitimacy, enabling attackers who steal credentials to access systems undetected. Zero Trust’s continuous verification dramatically reduces this risk.
Multi-factor authentication forms the first defense layer, requiring additional verification beyond passwords. But Zero Trust extends protection further through risk-based policies and session analytics that monitor for abnormal usage patterns. If a user’s credentials are used from an unusual location, at an odd time, or to access resources they don’t typically need, the system can immediately prompt for reauthentication, restrict access, or trigger incident response.
Modern implementations increasingly adopt passkeys—passwordless authentication using cryptographic keys tied to user devices. Passkeys eliminate the credentials that phishing attacks target, as there’s nothing for attackers to intercept or reuse remotely. This hardware-bound authentication blocks most common phishing vectors while improving user experience by eliminating password management.
Behavioral analytics complement authentication by continuously evaluating user actions. If an employee typically downloads modest amounts of data during business hours but suddenly attempts to exfiltrate gigabytes at 2 AM, anomaly detection systems trigger alerts and automatically restrict access. This active defense reduces the window attackers can exploit from hours to seconds.
Cloud native security architecture illustrating network segmentation, secure access, load balancing, and CI/CD integration with Jenkins and GitHub.
Implementation Roadmap: Your Path to Zero Trust
The Five-Phase Approach
Successfully implementing Zero Trust requires methodical planning and phased execution. Organizations that attempt “big bang” implementations often struggle with complexity, user resistance, and disruption to business operations. A structured five-phase approach, based on frameworks from Microsoft, NIST, and industry best practices, provides a proven path to Zero Trust maturity.
Phase 1: Inventory and Assessment of Assets (2-4 weeks) begins with thoroughly identifying and prioritizing critical business systems and services. Organizations must document all Data, Applications, Assets, and Services (DAAS elements), assessing current security maturity and potential impact of compromises. Tools like Microsoft Defender for Endpoint and Azure Security Center help inventory assets across networks. This phase also includes risk assessment to identify the most significant vulnerabilities requiring immediate attention.
Phase 2: Understand How Technology Drives Your Business (3-6 weeks) involves analyzing critical business systems and identifying dependencies. Teams map data flows, document interactions within and outside the “protect surface” (the area you intend to secure), and validate findings with stakeholders. Network traffic analysis tools and Security Information and Event Management (SIEM) systems help visualize how information moves through the organization. This mapping reveals effective points to apply Zero Trust protections.
Phase 3: Design Your Zero Trust Approach (4-8 weeks) aligns security objectives with business goals, selecting appropriate technologies and vendors that fit specific needs. Organizations define policies, rules, and workflows governing user, device, and application behavior. This phase emphasizes leveraging existing technology investments to maximize efficiency and cost-effectiveness. Azure Active Directory (Azure AD) and Conditional Access policies prove instrumental in defining and enforcing access policies.
Phase 4: Implement Your Design (3-6 months) creates Zero Trust security policies ensuring proper access control, starting with manageable quick wins to build momentum. Organizations prioritize use cases protecting the most critical DAAS elements, gradually expanding scope. A phased rollout minimizes disruption—many organizations adopt a department-by-department approach, ensuring each unit’s unique situation is addressed while minimizing business impact. Microsoft Intune and similar tools enforce device compliance policies across accessing devices.
Phase 5: Monitor and Maintain Your Environment (Ongoing) involves continuously reviewing and updating implemented policies, rules, and workflows based on key performance indicators and metrics. Active monitoring and improvement ensure Zero Trust architecture remains effective against evolving threats. Microsoft Sentinel and similar security platforms provide continuous monitoring and incident response capabilities essential for maintaining Zero Trust over time.
Starting Small: Finding Your Initial Use Case
Many organizations paralyze themselves trying to implement comprehensive Zero Trust across their entire environment simultaneously. Industry experts recommend identifying a focused initial use case that demonstrates value while building organizational experience.
Define clear objectives and goals by identifying your most critical assets and their vulnerabilities. Rather than attempting to secure everything, focus Zero Trust initiatives where they’ll have the greatest impact—protecting crown jewel data, securing privileged access, or enabling specific remote work scenarios. Measurable goals like reducing lateral movement by a specific percentage or enhancing threat detection times help track progress and justify continued investment.
Conduct proof-of-concept or proof-of-value engagements to validate selected solutions meet your requirements before full deployment. Test technologies on a limited scale, evaluating their effectiveness, user impact, and integration challenges. This pilot approach allows organizations to make informed decisions while minimizing risk.
Engage stakeholders early to foster support and address concerns about heightened oversight or procedural changes. Strong management involvement, with leadership actively communicating Zero Trust’s importance, proves essential for overcoming cultural resistance. Craft effective communication plans articulating advantages and reasoning for the transition, helping employees understand benefits rather than viewing it as burdensome oversight.
Overcoming Common Implementation Challenges
Organizations implementing Zero Trust encounter predictable challenges that can derail initiatives if not properly addressed. Understanding these obstacles and preparing appropriate responses dramatically improves success rates.
Cultural resistance emerges as employees and stakeholders prefer established practices and voice apprehensions about changes. Zero Trust’s continuous verification can feel like excessive surveillance, creating friction. Address this through structured change management techniques, behavioral tiered cybersecurity training tailored to user roles, and consistent messaging about protecting the organization and employees themselves. Having leadership actively champion Zero Trust initiatives signals organizational commitment.
Complexity of implementation and integration challenges many organizations, particularly those with legacy systems lacking compatibility with Zero Trust principles. A phased approach proves essential—assess current infrastructure, gradually roll out Zero Trust starting with critical assets, and expand systematically based on risk and business impact. Engaging experienced cybersecurity professionals to guide implementation helps navigate technical complexities.
Investment and budgeting concerns can be prohibitive, particularly for smaller organizations. The shift to Zero Trust sometimes necessitates large investments in new technology, training, and potentially reorganizing IT departments. However, viewing this as long-term investment rather than expense changes the calculation—the average data breach costs $4.45 million, and organizations with mature Zero Trust report 50% lower breach likelihood. The Forrester Total Economic Impact study found Zero Trust delivers 246% ROI over three years with payback in under six months.
Managing policies across multi-cloud environments emerged as the top challenge for 49% of organizations. Each cloud platform has unique tools, interfaces, and security requirements, making consistent policy enforcement difficult. Tools that simplify policy management and provide unified oversight across diverse environments are essential. Cloud-native Zero Trust solutions designed for multi-cloud architectures can significantly reduce this complexity.
Insufficient visibility across all environments hinders 34% of organizations, making threat detection and response difficult. Deploying comprehensive monitoring solutions that provide unified visibility across on-premises, cloud, and hybrid environments is critical. Real-time analytics platforms that correlate security events across all resources enable effective Zero Trust operations.
Business Value and Return on Investment
Quantifying Zero Trust Benefits
The financial case for Zero Trust extends far beyond avoiding breach costs, though that alone often justifies investment. A comprehensive analysis reveals multiple sources of value that collectively deliver compelling returns.
Breach cost avoidance represents the most significant financial benefit. With average global breach costs reaching $4.45 million—and higher in regions like the United States—Zero Trust’s 50% reduction in breach likelihood translates to substantial risk-adjusted savings. Organizations with mature Zero Trust implementations report saving an average of $1.76 million in breach costs compared to those without Zero Trust protections. A breach that might cost $5 million under traditional security could cost closer to $3.2 million with Zero Trust—a massive difference when considering risk-adjusted costs.
Infrastructure cost savings accrue as organizations consolidate security tools and eliminate redundant appliances. Moving to cloud-delivered Zero Trust models can reduce firewall and network hardware needs by up to 70%. Simplifying architecture also means fewer maintenance hours and lower management overhead, directly translating to operational cost savings. Organizations report up to 75% reduction in manual provisioning time through identity automation, freeing IT staff for strategic initiatives rather than routine access requests.
Productivity and operational efficiency gains emerge from improved user experiences and streamlined processes. Users accessing cloud applications often experience 3× faster access speeds after eliminating VPN bottlenecks. Faster, more reliable user experiences boost overall productivity and employee satisfaction while reducing IT support burdens. Automated policy enforcement reduces manual workloads, enabling lean IT teams to effectively secure complex environments without proportional headcount increases.
Compliance and audit efficiency provide additional value through automated compliance checking and simplified audits. Zero Trust architectures with tools like Microsoft Purview provide continuous compliance evidence, reducing man-hours and external consulting fees spent on audit preparation. The time-to-productivity for new hires improves through streamlined onboarding processes, and reduced IT support tickets related to access issues further cut operational costs.
Innovation acceleration enables organizations to adopt new technologies securely, bringing digital products and services to market faster. A Zero Trust framework provides guardrails for confidently migrating workloads to cloud platforms, building new applications, and participating in API economies. By embedding security directly into infrastructure, organizations can accelerate development cycles knowing systems are secure by design.
The ROI Equation
Industry studies consistently demonstrate strong returns on Zero Trust investments. The Forrester Total Economic Impact study found organizations implementing Zero Trust architecture achieved an average 246% ROI over three years, with initial investment paid back in well under six months. This remarkable return stems from the combination of avoided breach costs, eliminated legacy security tools, improved user productivity, and security operations efficiencies.
For mid-market organizations—those facing enterprise-level threats with small business resources—Zero Trust represents particularly strong strategic value. The framework protects business continuity by reducing breach chances and containing damage, preventing the days of downtime that could threaten company survival. A well-implemented Zero Trust architecture actually simplifies security management over time, with centrally-managed platforms replacing tangled arrays of disparate security tools.
Perhaps most importantly, Zero Trust enables the modern work organizations need—supporting remote employees, cloud migration, and mobile workforces—without forcing trade-offs between security and agility. Traditional security sometimes created binary choices: strict controls that hurt user experience, or lax controls to avoid hampering productivity. Zero Trust balances security and usability through silent verification running in the background while connecting users directly to needed resources.
Measuring Success: Key Performance Indicators
Organizations implementing Zero Trust should establish clear metrics to track progress and demonstrate value. Effective KPIs span technical security improvements, operational efficiency gains, and business impact measures.
Security posture metrics include reduction in successful phishing attempts, time-to-detect security incidents, mean time to respond to threats, and percentage of users with MFA enabled. Organizations should track the number of access policy violations, lateral movement attempts blocked, and critical vulnerabilities remediated. Mature Zero Trust implementations show measurable improvements across all these dimensions.
Operational efficiency indicators measure manual provisioning time reduction, IT support tickets related to access issues, and time-to-productivity for new employees. Tracking the reduction in security tool sprawl and associated management overhead demonstrates operational value. User satisfaction scores and application access speed provide insight into whether security improvements come at productivity costs.
Business impact measures include avoided breach costs, compliance audit preparation time, time-to-market for new digital services, and secure adoption rate of cloud services. Calculating risk-adjusted security costs—comparing potential breach expenses against Zero Trust investment—provides clear financial perspective on ROI.
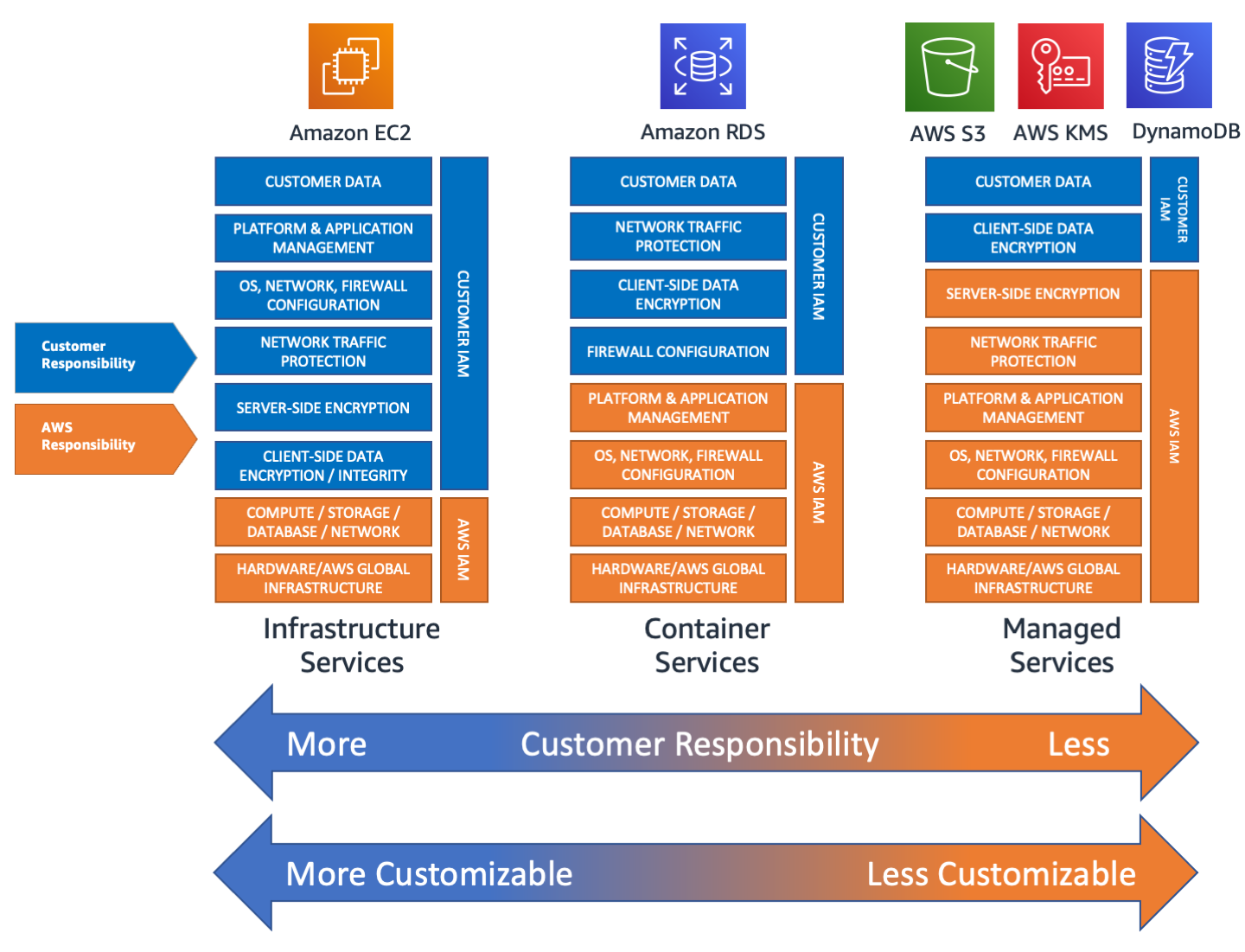
Shared responsibility and customer vs AWS security roles across AWS infrastructure, container, and managed services.
The Future of Zero Trust: Emerging Trends and Technologies
Artificial Intelligence and Machine Learning Integration
The convergence of AI/ML technologies with Zero Trust principles is creating more intelligent, adaptive security frameworks. While Zero Trust establishes the architectural foundation of continuous verification and least-privilege access, AI makes security systems proactive rather than merely reactive.
Anomaly detection powered by machine learning excels at identifying patterns and deviations that signal potential compromise. By establishing baselines of normal behavior across users, devices, and applications, AI immediately recognizes suspicious activities that might indicate breach—often before traditional security tools raise alarms. These systems learn continuously from experience, becoming more effective at recognizing increasingly complex attack patterns over time.
Predictive analytics move beyond addressing current threats to forecasting potential security incidents before they materialize. AI analyzes historical data, current trends, and threat intelligence to identify likely attack vectors and vulnerable assets, enabling proactive defense rather than reactive response. Organizations can strengthen defenses where AI predicts attackers will strike rather than waiting for incidents to occur.
Automated threat response represents perhaps AI’s most significant contribution to Zero Trust. When threats emerge, AI can initiate immediate defensive actions—step-up authentication, session termination, network isolation, or privilege revocation—without human intervention. This automation dramatically reduces response time from hours to seconds, containing threats before they spread. Incident response playbooks executed by AI allow organizations to rapidly identify and neutralize threats, a core capability of mature Zero Trust architectures.
Adaptive access controls leverage AI to dynamically adjust security requirements based on real-time risk assessment. Rather than static policies, AI-driven systems calculate continuous trust scores by evaluating user behavior, device health, contextual factors, and threat intelligence. Access levels automatically adjust as risk profiles change—a user exhibiting unusual behavior faces heightened authentication requirements, while normal patterns enable frictionless access.
Quantum Computing and Post-Quantum Cryptography
The emergence of quantum computing presents both threats and opportunities for Zero Trust architectures. Quantum computers’ ability to break current encryption algorithms threatens the cryptographic foundations on which Zero Trust relies—identity verification, data protection, and secure communications all depend on encryption that quantum systems could compromise.
Forward-thinking organizations are already exploring quantum-enhanced Zero Trust frameworks. Quantum key distribution provides theoretically unbreakable encryption, offering more robust network protection particularly as quantum computing advances. The integration of quantum technology with Zero Trust principles could establish fundamentally more secure architectures, effectively countering both classical and quantum-based attacks.
Research in quantum fingerprinting for device authentication adds another layer of protection. This approach leverages quantum properties to create unforgeable device identities, preventing MAC spoofing and device impersonation attacks that plague traditional authentication systems. As quantum technology matures, its incorporation into Zero Trust frameworks will likely become essential for organizations handling highly sensitive information.
Blockchain and Distributed Zero Trust
Blockchain technology offers promising enhancements to Zero Trust architectures, particularly for identity management and policy enforcement. Blockchain-based identity systems provide tamper-resistant, decentralized authentication that eliminates single points of failure in traditional identity platforms. Every identity verification and access decision can be immutably recorded, creating comprehensive audit trails that support compliance and forensic investigation.
Smart contracts enable automated policy enforcement without centralized authority. Access policies encoded in smart contracts execute automatically when predefined conditions are met, ensuring consistent enforcement across distributed environments. This decentralization proves particularly valuable in multi-organization collaborations where no single entity controls security infrastructure.
Research into blockchain-enhanced Zero Trust for supply chains demonstrates practical applications. Supply chain security requires trust verification across multiple organizations and systems, making centralized Zero Trust challenging. Blockchain provides secure, transparent record-keeping and automated transaction execution, combined with Zero Trust’s continuous verification to create resilient supply chain security frameworks.
Expanding to Edge Computing and IoT
The explosion of edge computing and IoT devices presents unique challenges for Zero Trust implementation. These resource-constrained devices often lack computational power for traditional security measures, yet their proliferation creates massive attack surfaces requiring protection.
Lightweight Zero Trust protocols designed specifically for IoT balance security with device limitations. These solutions provide authentication and access control without overwhelming device resources, enabling Zero Trust principles even on sensors and actuators with minimal processing capability. Research into optimized cryptographic approaches continues to improve feasibility of IoT Zero Trust.
Zero Trust frameworks for IoT actuators—devices that affect the physical world—prove particularly critical. Traditional security that treats IoT devices as monitoring-only systems fails to address risks from compromised actuators that could cause physical damage. Zero Trust architectures for actuators implement strict control verification, ensuring commands originating from cyber space undergo rigorous authentication before affecting physical systems.
The Role of Zero Trust in 6G Networks
As telecommunications evolve toward 6G, Zero Trust principles are being architected into next-generation network designs from inception. The distributed, heterogeneous nature of 6G networks—with billions of connected devices, edge computing nodes, and network slices supporting diverse services—makes perimeter-based security completely impractical.
Software-defined Zero Trust architectures proposed for 6G provide elastic, scalable security through adaptive collaborations among control domains. These architectures achieve secure access control through dynamic policy enforcement, effectively preventing malicious access behaviors across the highly distributed 6G ecosystem. Zero Trust frameworks for 6G Multi-Access Edge Computing demonstrate how trust evaluation of network behavior enables secure application access.
The “Age of Trust” concept introduced for wireless networks captures how trust degrades over time, requiring adaptive verification strategies. Rather than one-time authentication, 6G Zero Trust continuously evaluates trust levels, adjusting verification frequency based on changing risk profiles. This dynamic approach balances security requirements against network efficiency, optimizing both protection and performance.
Call to Action: Partner with Experts for Your Zero Trust Journey
The path to Zero Trust can seem daunting, but you don’t have to navigate it alone. The complexity of modern IT environments, the diversity of available technologies, and the criticality of getting security right make expert guidance invaluable for organizations beginning their Zero Trust transformation.
Ready to transform your security posture? Reach out to our Zero Trust consultancy team to begin your journey toward comprehensive, adaptive cybersecurity that protects your organization in today’s threat landscape and tomorrow’s challenges.